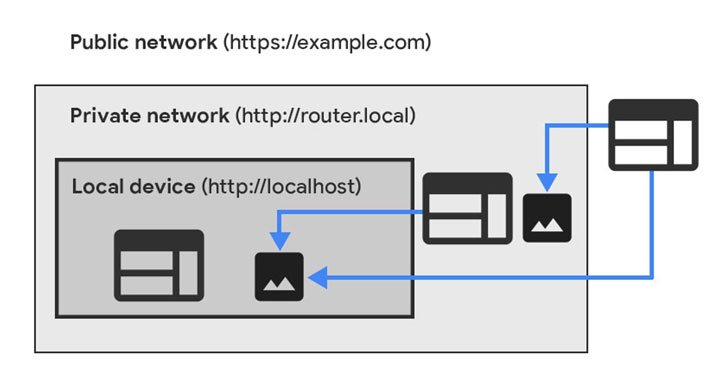
Google Chrome has announced plans to prohibit public websites from directly accessing endpoints located within private networks as part of an upcoming major security shakeup to prevent intrusions via the browser. The proposed change is set to be rolled out in two phases as part of releases Chrome 98 and Chrome 101 scheduled in the coming months via a newly implemented W3C specification called private network...
Read More
January 2022
There are three major players when it comes to patch management: security analysts, IT professionals, and attackers. And unfortunately, there is usually a lot of friction between the security and IT teams, preventing them from successfully defending against the attackers. This leads to an asymmetric threat where an attacker only needs to know one weakness or vulnerability to be successful, while the defenders must know...
Read MoreThreat actors are actively incorporating public cloud services from Amazon and Microsoft into their malicious campaigns to deliver commodity remote access trojans (RATs) such as Nanocore, Netwire, and AsyncRAT to siphon sensitive information from compromised systems. The spear-phishing attacks, which commenced in October 2021, have primarily targeted entities located in the U.S., Canada, Italy, and Singapore, researchers from Cisco Talos said in a report shared with...
Read MoreThe director for the Academic Center for Computing and Media Studies within the Institute for Information Management and Communication at Japan’s Kyoto University, Toshio Okabe, issued an apology on December 28 to users of the supercomputing systems for losing approximately 77 terabytes of user data, which comprised approximately a mere 34 million files from 14 research groups. The apology follows the advisory that users had received...
Read MoreWe now live in a world where cyberattacks can shut down critical infrastructure. Those who follow the mega-trends driving the global economy — like the convergence of the digital revolution and the energy transition — understand that with more and more critical infrastructure remotely operated or digitally managed, it was only a matter of time before a cyberattack caused disruptions that crossed over into the...
Read MoreThe Apache Log4j vulnerability has made global headlines since it was discovered in early December. The flaw has impacted vast numbers of organizations around the world as security teams have scrambled to mitigate the associated risks. Here is a timeline of the key events surrounding the Log4j vulnerability as they have unfolded. Thursday, December 9: Apache Log4j zero-day exploit discoveredApache released details on a critical vulnerability...
Read More