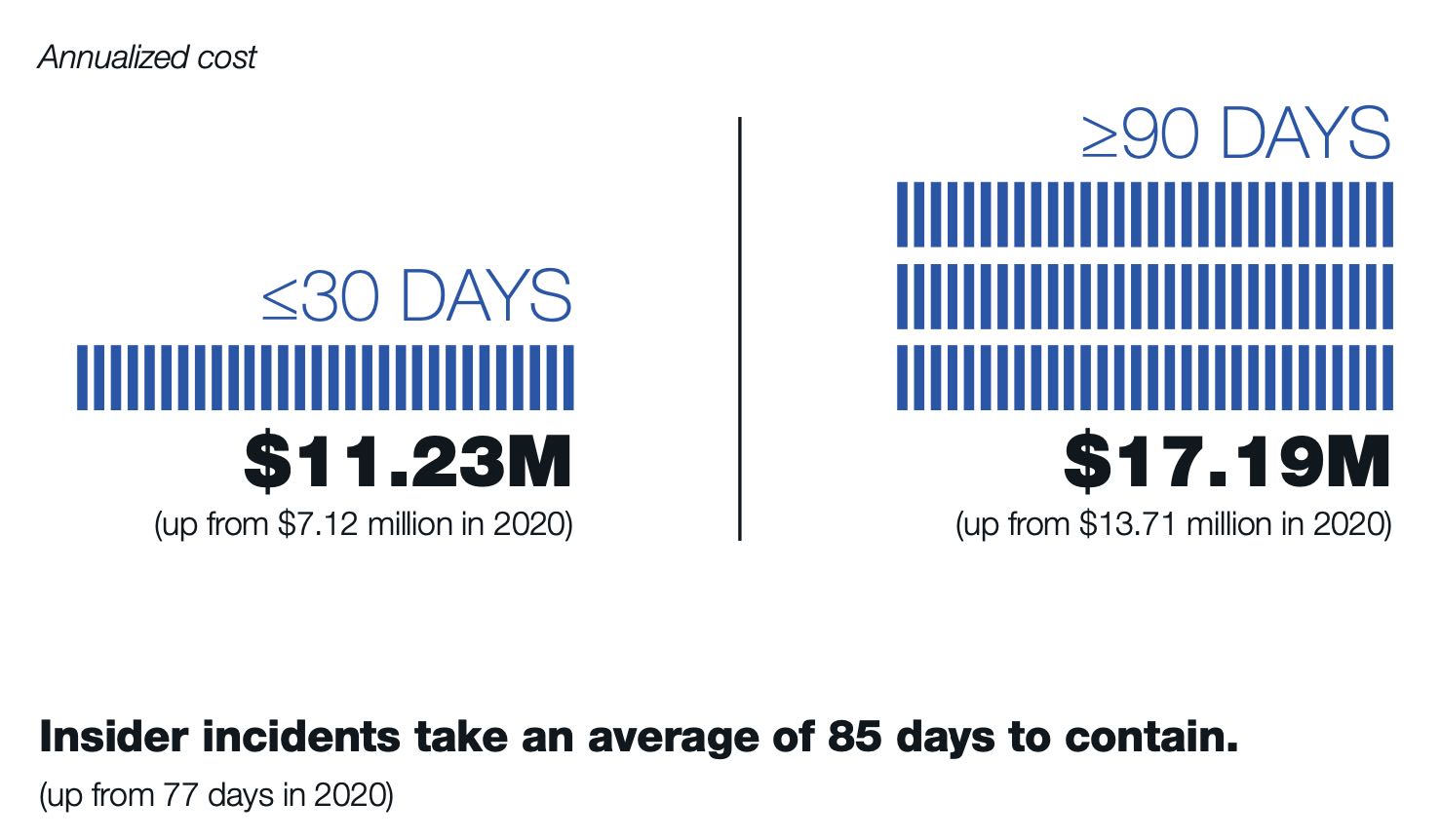
Organizations dealing with insider threats spent $15.4 million on average during 2021, a 34% increase from 2020, and required 85 days to contain each incident, according to a survey of 1,000 information technology and security professionals released on Jan. 25. The survey, conducted by the Ponemon Institute and sponsored by enterprise security firm Proofpoint, documented 6,803 total insider incidents, including those caused by negligent employees, malicious...
Read More
February 2022
A gang of cybercriminals known for breaking into computer systems and selling access to them has been discovered exploiting an Apache Log4j vulnerability, Log4Shell, in unpatched VMware Horizon to plant cryptominers and backdoors on targeted systems. In a blog published Wednesday, Blackberry' researchers Ryan Gibson, Codi Starks and Will Ikard revealed that Prophet Spider was behind the attacks, which could be reliably detected by monitoring ws_TomcatService.exe,...
Read MoreThere are three things you can be sure of in life: death, taxes – and new CVEs. For organizations that rely on CentOS 8, the inevitable has now happened, and it didn't take long. Just two weeks after reaching the official end of life, something broke spectacularly, leaving CentOS 8 users at major risk of a severe attack – and with no support from CentOS. You'd...
Read MoreLatest analysis into the wiper malware that targeted dozens of Ukrainian agencies earlier this month has revealed "strategic similarities" to NotPetya malware that was unleashed against the country's infrastructure and elsewhere in 2017. The malware, dubbed WhisperGate, was discovered by Microsoft last week, which said it observed the destructive cyber campaign targeting government, non-profit, and information technology entities in the nation, attributing the intrusions to an...
Read MoreResearchers uncovered a stealthy UEFI rootkit that's being used in highly targeted campaigns by a notorious Chinese cyberespionage group with suspected government ties. The group is known for using software supply-chain attacks in the past. Dubbed MoonBounce by researchers from Kaspersky Lab, the implant's goal is to inject a malicious driver into the Windows kernel during the booting stages, providing attackers with a high level...
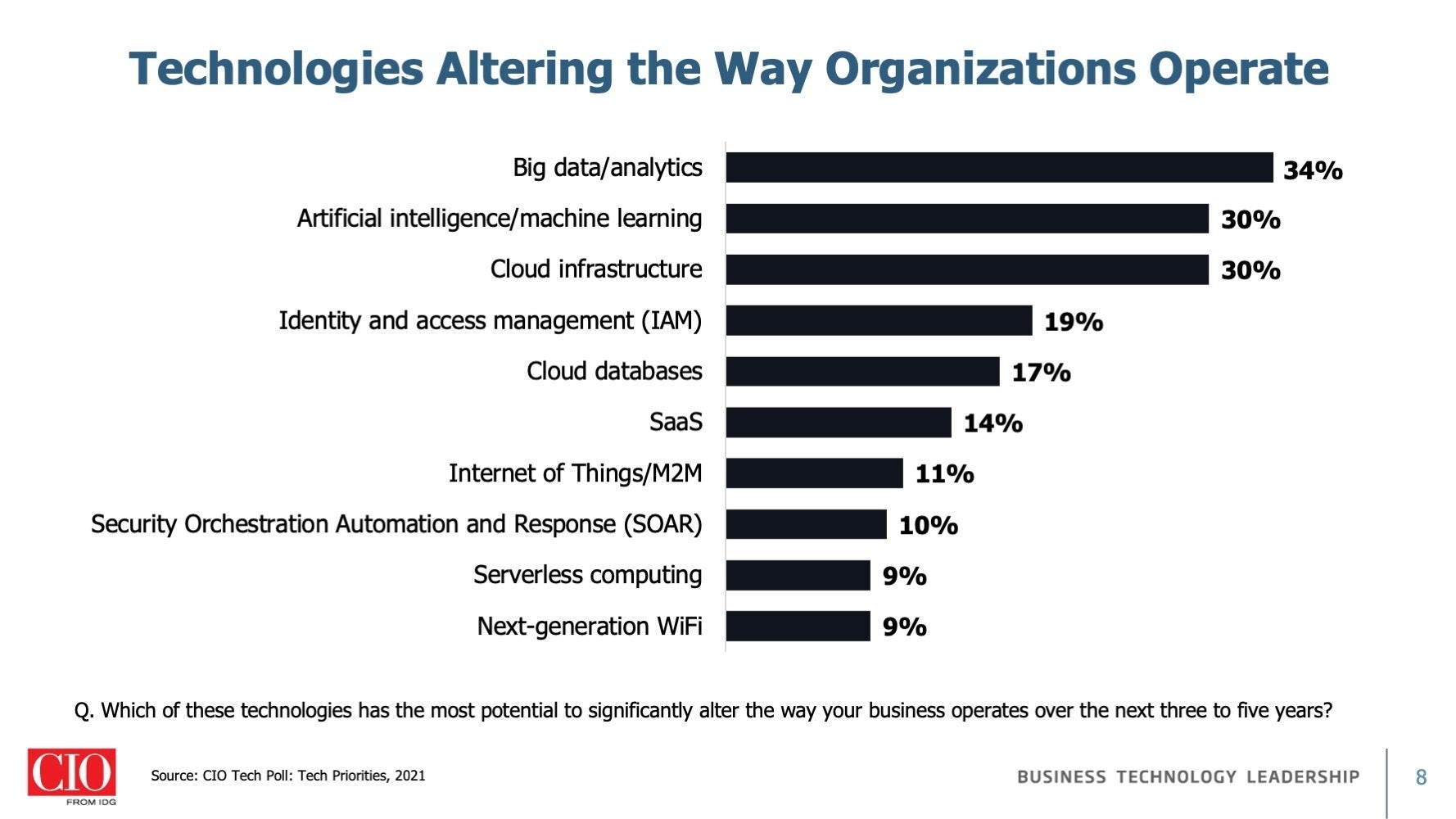
Read MoreWith new threats disrupting business operations and an increasingly strict regulatory environment, security is no longer a risk mitigation activity or a growth inhibitor. Rather, information security is increasingly being viewed as strategic business enabler for the enterprise. That is evident in IDG's 2022 State of the CIO Survey, where IT leaders and line of business (LOB) executives were asked which technologies they expected to have...
Read MoreMany organizations accelerated digital transformation in response to COVID-19 to remain resilient and competitive, with heavy investments in the cloud. This trend will continue well beyond the initial stages of the pandemic, with IDC's spending forecast on "whole cloud" services to surpass $1.3 trillion by 2025. Unfortunately, side effects from these expanded architectures include enhanced risk of shadow IT and unauthorized cloud access, as well as...
Read More