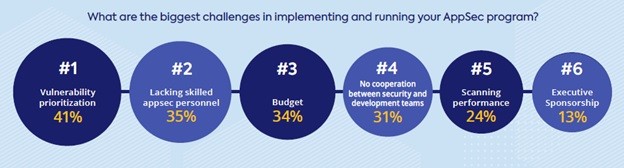
Why vulnerability prioritization has become a top challenge for security professionals and how security and development teams can get it right. When it comes to addressing their backlog of unfixed security issues, many software development organizations are facing an uphill battle. One reason is the proliferation of automated security tools. Adopting automated solutions helps developers and security shift testing left and eliminate time-consuming manual processes, and...
Read More
Cybersecurity
Despite a recent decline in attacks, ransomware still poses significant threats to enterprises, as the attacks against healthcare organizations demonstrated this month. It is also becoming more capable. In particular, ransomware writers are aware that backups are an effective defense and are modifying their malware to track down and eliminate the backups. Ransomware targeting backups Ransomware will now delete any backups it happens to come across along...
Read MoreOne of the smartest moves you can make to protect employees, especially those working from home, is to encourage them to use a password manager. It’s one of the easiest, too. Keyword best practices pertain to complexity, change frequency and uniqueness. Each best practice is intended to mitigate known attack methods and harden your online identities to both prevent compromise and limit the damage if account...
Read MoreVirtual appliances are a popular way for software vendors to distribute their products to enterprise customers as they contain all the necessary pre-configured software stacks their applications need to function and can be deployed in public clouds or private data centers with ease. Unfortunately, enterprises are at risk of deploying images that are vulnerable out-of-the-box according to a new study. It found that many vendors,...
Read MoreAs businesses are increasingly migrating to the cloud, securing the infrastructure has never been more important. Now according to the latest research, two security flaws in Microsoft's Azure App Services could have enabled a bad actor to carry out server-side request forgery (SSRF) attacks or execute arbitrary code and take over the administration server. "This enables an attacker to quietly take over the App Service's git server,...
Read MoreIf you're administrating Windows Server, make sure it's up to date with all recent patches issued by Microsoft, especially the one that fixes a recently patched critical vulnerability that could allow unauthenticated attackers to compromise the domain controller. Dubbed 'Zerologon' (CVE-2020-1472) and discovered by Tom Tervoort of Secura, the privilege escalation vulnerability exists due to the insecure usage of AES-CFB8 encryption for Netlogon sessions, allowing remote attackers...
Read MoreFacebook has patched a bug in its widely installed Messenger app for Android that could have allowed a remote attacker to call unsuspecting targets and listen to them before even they picked up the audio call. The flaw was discovered and reported to Facebook by Natalie Silvanovich of Google's Project Zero bug-hunting team last month on October 6 with a 90-day deadline, and impacts version 284.0.0.16.119...
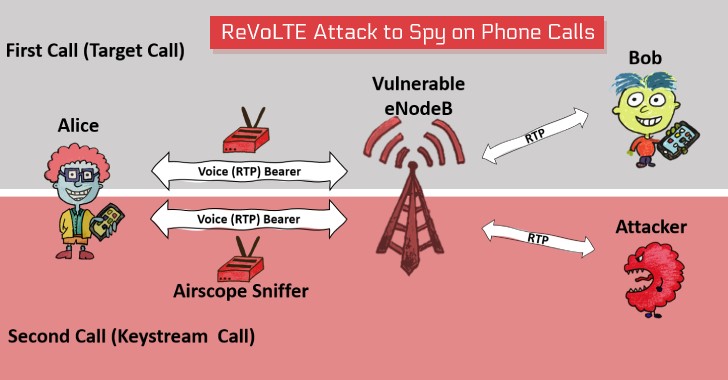
Read MoreA team of academic researchers—who previously made the headlines earlier this year for uncovering severe security issues in the 4G LTE and 5G networks—today presented a new attack called 'ReVoLTE,' that could let remote attackers break the encryption used by VoLTE voice calls and spy on targeted phone calls. The attack doesn't exploit any flaw in the Voice over LTE (VoLTE) protocol; instead, it leverages weak implementation...
Read MoreLike the universe, the attack surface is always expanding. Here's how to keep up and even get ahead. Most criminal activity is designed to elicit a payoff for the perpetrator, and crime on the Internet is no different. As new surfaces emerge, previous attacks are reconstituted and applied. Cybersecurity tends to follow a cycle, once you know when and what to look for. To (poorly) paraphrase...
Read MorePopular video conferencing app Zoom recently fixed a new security flaw that could have allowed potential attackers to crack the numeric passcode used to secure private meetings on the platform and snoop on participants. Zoom meetings are by default protected by a six-digit numeric password, but according to Tom Anthony, VP Product at SearchPilot who identified the issue, the lack of rate limiting enabled "an attacker...
Read More