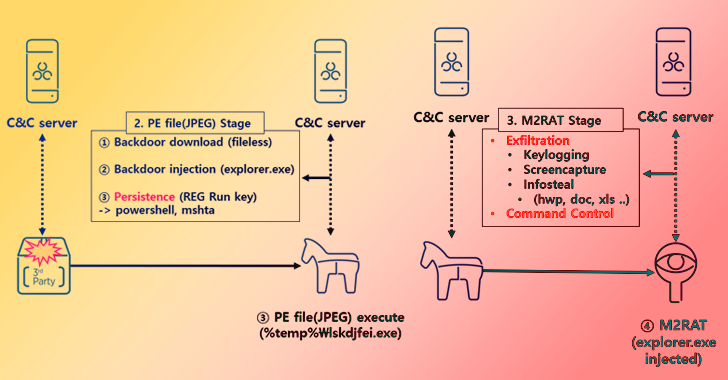
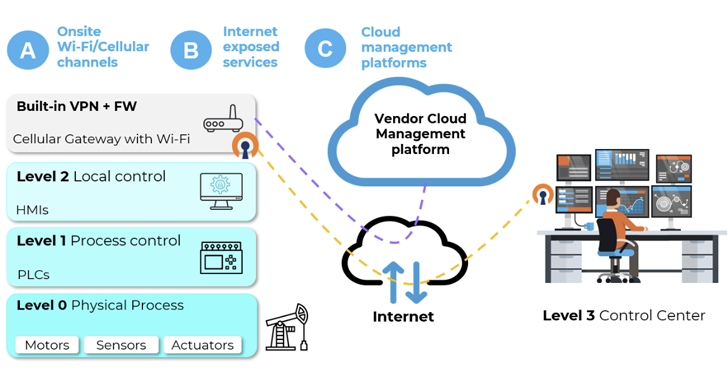
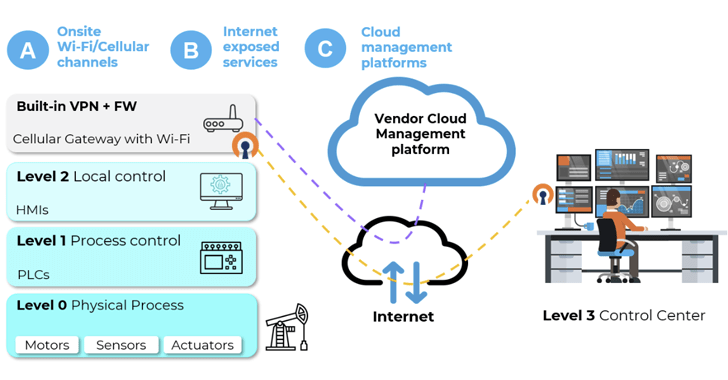
Have the Bad Guys done a number on the Good Guys? The Good Guys has become the latest company to reveal that its customers have been affected by a data breach that occurred at My Rewards - a 3rd part loyalty program provider. The breach, which occurred in August 2021, exposed limited customer data such as names, addresses, phone numbers and email addresses. In some cases, an...
Read More
Cybersecurity
On February 23, 2023, multiple threat actors have been observed exploiting a critical security vulnerability impacting several Zoho ManageEngine products since January 20, 2023. Tracked as CVE-2022-47966 (CVSS score: 9.8), the remote code execution flaw allows a complete takeover of the susceptible systems by unauthenticated attackers. Martin Zugec of Bitdefender's cybersecurity firm revealed in a technical advisory that the vulnerability "allows unauthenticated remote code execution due...
Read MoreChina-based cyberespionage actor DEV-0147 has been observed compromising diplomatic targets in South America, according to Microsoft’s Security Intelligence team. The initiative is “a notable expansion of the group’s data exfiltration operations that traditionally targeted gov’t agencies and think tanks in Asia and Europe,” the team tweeted on Monday. DEV-0147’s attacks in South America included post-exploitation activity involving the abuse of on-premises identity infrastructure for reconnaissance...