Heads up for network administrators with F5’s BIG-IP family of networking devices in their environment: There is a new security update available for the newly disclosed critical remote code execution vulnerability (CVE-2022-1388). Several security researchers have already created working exploits, so administrators need to move quickly and secure their networks before the attackers come knocking. According to security researcher Kevin Beaumont, attackers are already trying to...
Read More
Cybersecurity
The transition into CWPP Agility and flexibility were key directives in the development of new technology, which is why on-premise assets soon transitioned into virtual machines, which further transformed into compact and swift containers. Modern enterprise network environments are increasingly transforming to be cloud-based, where both applications and data storage are hosted in a cloud — and often multi-cloud — environment. The attack surfaces and...
Read MoreCisco Systems on Wednesday shipped security patches to contain three flaws impacting its Enterprise NFV Infrastructure Software (NFVIS) that could permit an attacker to fully compromise and take control over the hosts. Tracked as CVE-2022-20777, CVE-2022-20779, and CVE-2022-20780, the vulnerabilities "could allow an attacker to escape from the guest virtual machine (VM) to the host machine, inject commands that execute at the root level, or leak...
Read MoreSecurity experts have been banging the multifactor authentication drum for years, encouraging users to move away from just relying on the username/password combination to secure their most sensitive accounts. Now GitHub is done with encouraging: By the end of 2023, all users who contribute code to GitHub-hosted repositories must have one or more forms of two-factor authentication enabled, the company says. Zero-day attacks and sophisticated exploits...
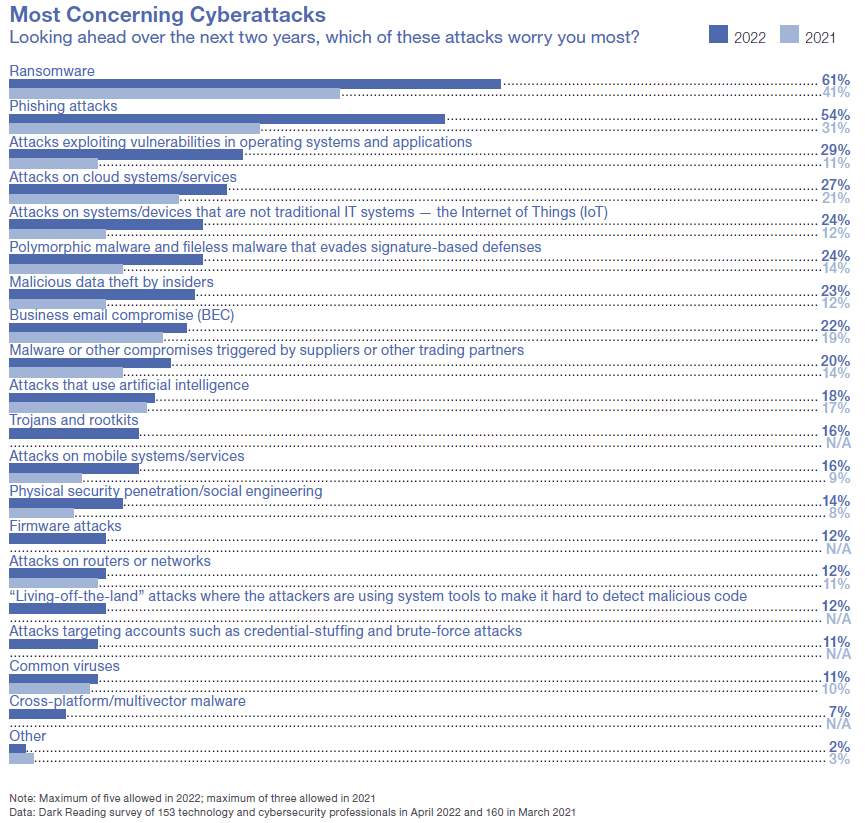
Read MoreBig picture, security professionals worry about how to defend their organizations against increasingly sophisticated attacks exploiting zero-day vulnerabilities or nation-state attackers, but their day-to-day security concerns appear to be far more prosaic. According to Dark Reading's "The State of Malware Threats" report, ransomware and phishing attacks are top-of-mind for security professionals. When asked which type of attacks worried them most, 61% of IT security professionals cited...
Read MoreThe need for organisations to guard against the dangers of ransomware is not new, yet never has the threat to data been so pervasive as in 2022. In addition to the perpetually ongoing growth in the scale and sophistication of the capabilities which threat actors possess, there’s been the requirement for businesses to rapidly shift to work-from-home models since the outbreak of the Covid-19 pandemic –...
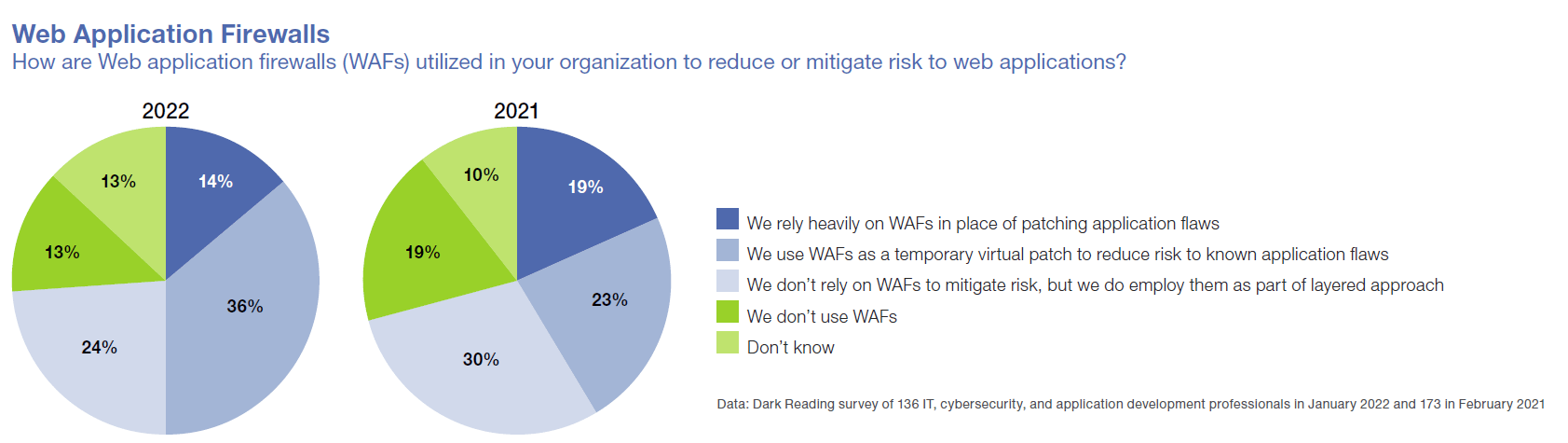
Read MoreThe ongoing struggle to update vulnerable software by finding and applying the right patches in a timely manner has led half of enterprise IT departments to use Web application firewalls (WAFs) either in lieu of patching or to offer some protection before patching can be achieved. This comes from a new Dark Reading report, "How Enterprises Are Securing the Application Environment." The survey asked 136 IT,...
Read MoreA financially motivated threat actor has been observed deploying a previously unknown rootkit targeting Oracle Solaris systems with the goal of compromising Automatic Teller Machine (ATM) switching networks and carrying out unauthorized cash withdrawals at different banks using fraudulent cards. Threat intelligence and incident response firm Mandiant is tracking the cluster under the moniker UNC2891, with some of the group's tactics, techniques, and procedures sharing overlaps...
Read MoreAs many as 722 ransomware attacks were observed during the fourth quarter of 2021, with LockBit 2.0, Conti, PYSA, Hive, and Grief emerging as the most prevalent strains, according to new research published by Intel 471. The attacks mark an increase of 110 and 129 attacks from the third and second quarters of 2021, respectively. In all, 34 different ransomware variants were detected during the three-month-period...
Read MoreThree months after the Apache Foundation disclosed the infamous Lo4j vulnerability [CVE-2021-44228] and issued a fix for it, more than 4 in 10 downloads of the logging tool from the Maven Central Java package repository continue to be known vulnerable versions. A dashboard that Maven Central administrator Sonatype launched soon after news of the so-called Log4Shell flaw first surfaced shows that 41% of Log4j packages downloaded...
Read More