IT Leaders Consider Security Tech a Part of Business Transformation
With new threats disrupting business operations and an increasingly strict regulatory environment, security is no longer a risk mitigation activity or a growth inhibitor. Rather, information security is increasingly being viewed as strategic business enabler for the enterprise.
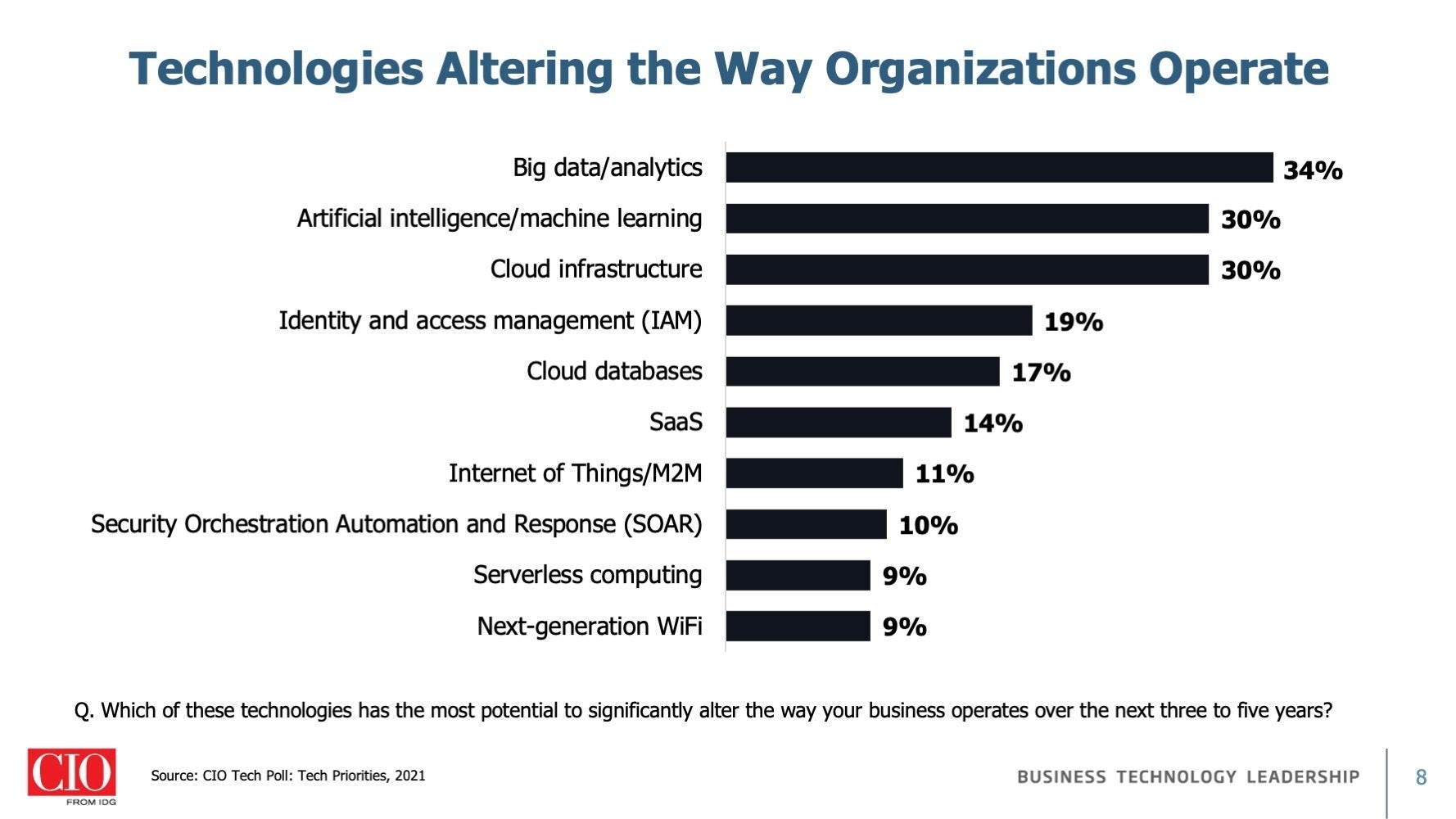
That is evident in IDG’s 2022 State of the CIO Survey, where IT leaders and line of business (LOB) executives were asked which technologies they expected to have the greatest effect on how their company functions over the next few years. While the respondents list the usual suspects – big data/analytics, AI/machine learning, and cloud infrastructure – in the top 3, 19% say identity and access management has the most potential to significantly impact business operations.
In a distributed world, identity and access management (IAM) is instrumental in managing security in a cloud-based world, which makes its placement between cloud infrastructure and cloud databases (picked by 17% of respondents) appropriate. Software-as-a-service (SaaS) comes in at 14%, in yet more evidence that IT professionals expect remote access to remain the new normal, with its benefits to both users and administrators outweighing its risks. IT leaders are recognizing that without a way to securely manage identity and block unauthorized access, business operations will be left wide open for attack.
Security orchestration, automation, and response (SOAR) earns a mention from 10%, in another nod to cloud security. SOAR services allow analysts to triage caseloads by using information collected by other security tools and automating the response. Its importance to enterprise is underscored by the fact that Google reportedly paid $500 million for Siemplify earlier this month to add SOAR capabilities to Google Cloud.
It’s also worth noting that security is part of the conversation for big data and analytics, as well as AI and machine learning. The explosion of devices and growing number of attacks means security teams are relying on data analytics to combine log data from endpoints, applications, and network tools to look for correlations and anomalies that may suggest attacks or other security issues. Similarly, security teams are increasingly using AI and machine learning tools to improve threat detection and response.

