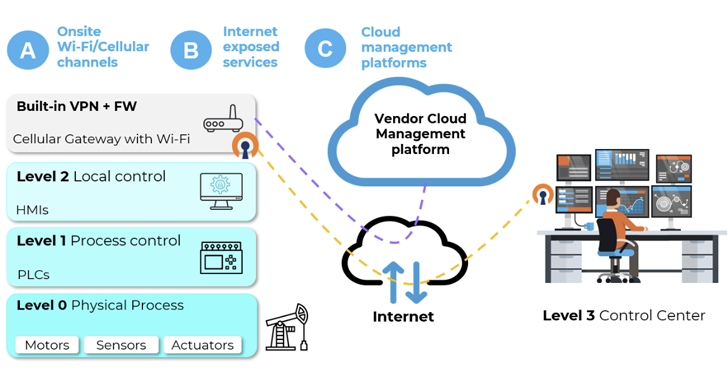
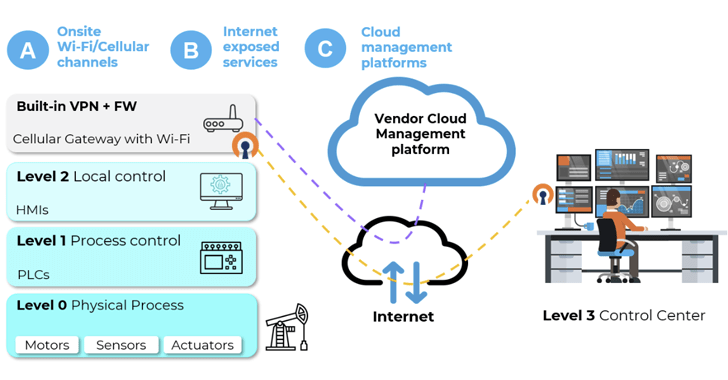
The US Cybersecurity and Infrastructure Security Agency (CISA) has released seven advisories this week about vulnerabilities in industrial control systems (ICS) and supervisory control and data acquisition (SCADA) software from various vendors. These advisories cover critical flaws, two of which have public exploits. The affected products include ScadaFlex II controllers made by Industrial Control Links, Screen Creator Advance 2 and Kostac PLC programming software from JTEKT...
Read More
Critical Infrastructure Tag
An international law enforcement operation has taken down Genesis Market, a notorious illegal online marketplace that traded in stolen credentials such as email, bank account, and social media platform information. The operation, codenamed Operation Cookie Monster, involved 17 countries and resulted in 119 arrests and 208 property searches across 13 nations. Since its inception in March 2018, Genesis Market has become a major hub for criminal...
Read MoreA new information stealer called SYS01stealer has been discovered by cybersecurity researchers, targeting critical government infrastructure employees, manufacturing companies, and other sectors. The attack is designed to steal sensitive information, including login data, cookies, and Facebook ad and business account information. The Israeli cybersecurity company Morphisec reported that the campaign was initially tied to a financially motivated cybercriminal operation dubbed Ducktail by Zscaler. However, WithSecure, which...
Read More