Wireless IIoT Device Vulnerabilities Pose Risk to Critical Infrastructure
On February 9th, 2023, Otorio, an Israeli industrial cybersecurity company, uncovered a set of 38 security vulnerabilities in four different vendors’ wireless industrial internet of things (IIoT) devices. These flaws could present a significant attack surface for threat actors looking to exploit operational technology (OT) environments.
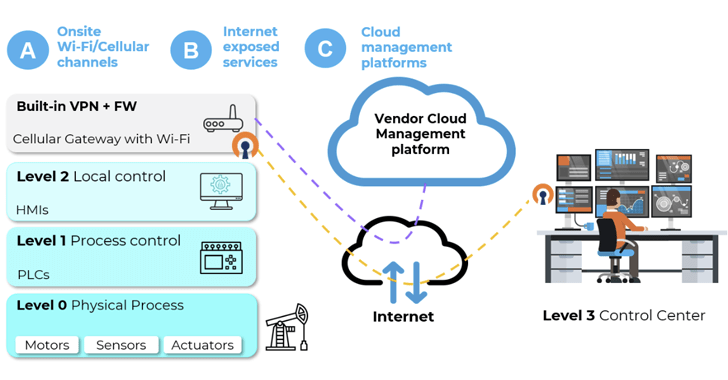
The vulnerabilities offer a remote entry point for attack, enabling unauthenticated adversaries to gain a foothold and subsequently use it as leverage to spread to other hosts, thereby causing significant damage. Of the 38 defects, three affect ETIC Telecom’s Remote Access Server (RAS), five concern InHand Networks’ InRouter 302 and InRouter 615, and two affect Sierra Wireless AirLink Router. The remaining flaws are still under responsible disclosure.
These findings underscore how OT networks could be put at risk by making IIoT devices directly accessible on the internet, creating a “single point of failure” that can bypass all security protections. Alternatively, local attackers can break into industrial Wi-Fi access points and cellular gateways by targeting on-site Wi-Fi or cellular channels, leading to adversary-in-the-middle (AitM) scenarios with adverse potential impact.
To protect against these attacks, Otorio recommends disabling insecure encryption schemes, hiding Wi-Fi network names, disabling unused cloud management services, and taking steps to prevent devices from being publicly accessible. This development comes after Otorio disclosed details of two high-severity flaws in Siemens Automation License Manager that were patched by Siemens in January 2023.

