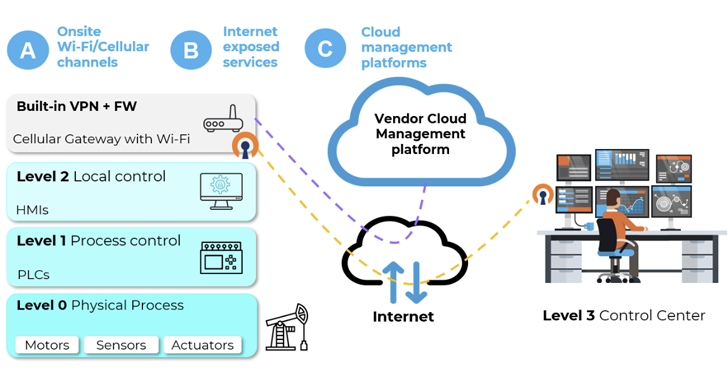
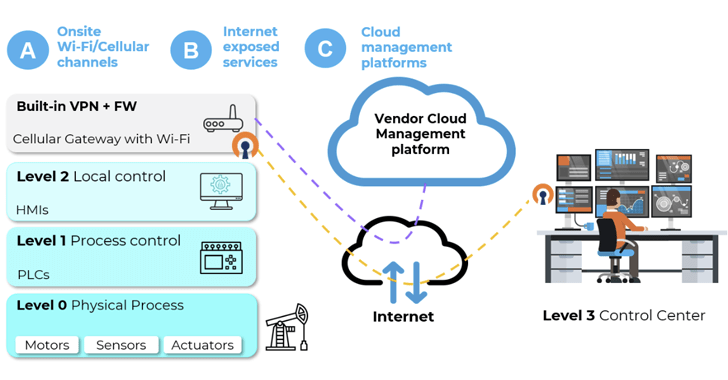
The US Cybersecurity and Infrastructure Security Agency (CISA) has released seven advisories this week about vulnerabilities in industrial control systems (ICS) and supervisory control and data acquisition (SCADA) software from various vendors. These advisories cover critical flaws, two of which have public exploits. The affected products include ScadaFlex II controllers made by Industrial Control Links, Screen Creator Advance 2 and Kostac PLC programming software from JTEKT...
Read More
critical Tag
An international law enforcement operation has taken down Genesis Market, a notorious illegal online marketplace that traded in stolen credentials such as email, bank account, and social media platform information. The operation, codenamed Operation Cookie Monster, involved 17 countries and resulted in 119 arrests and 208 property searches across 13 nations. Since its inception in March 2018, Genesis Market has become a major hub for criminal...
Read MorePopular e-commerce plug-in, WooCommerce, used for WordPress-based online stores, has been found to contain a critical vulnerability that could allow attackers to take over websites. While technical details about the vulnerability have not been published, the WooCommerce team has released updates, and attackers could reverse-engineer the patch. The vulnerability allows for unauthenticated administrative takeover of websites. Website administrators using this plugin are advised to issue the...
Read MoreMicrosoft Releases 76 Fixes in Latest Patch Tuesday Collection. Microsoft has released a collection of 76 fixes for various vulnerabilities as part of its Patch Tuesday update. Of these, two bugs are currently under active exploitation. One of the bugs, CVE-2023-23415, appears to be a “ping of death” and is an ICMP remote code execution (RCE) vulnerability with a CVSS score of 9.8. Attackers can exploit this...
Read MoreA new information stealer called SYS01stealer has been discovered by cybersecurity researchers, targeting critical government infrastructure employees, manufacturing companies, and other sectors. The attack is designed to steal sensitive information, including login data, cookies, and Facebook ad and business account information. The Israeli cybersecurity company Morphisec reported that the campaign was initially tied to a financially motivated cybercriminal operation dubbed Ducktail by Zscaler. However, WithSecure, which...
Read MoreThe security of Fortinet FortiNAC appliances is under attack, with proof-of-concept exploit code now available and active exploitation attempts in the wild. FortiNAC is a zero-trust network access solution that can be deployed both as a hardware device or as a virtual machine appliance, and is used for network segmentation, visibility, and control of devices and users connected to the network. With more than 700,000 Fortinet...
Read MoreOn February 23, 2023, multiple threat actors have been observed exploiting a critical security vulnerability impacting several Zoho ManageEngine products since January 20, 2023. Tracked as CVE-2022-47966 (CVSS score: 9.8), the remote code execution flaw allows a complete takeover of the susceptible systems by unauthenticated attackers. Martin Zugec of Bitdefender's cybersecurity firm revealed in a technical advisory that the vulnerability "allows unauthenticated remote code execution due...
Read More