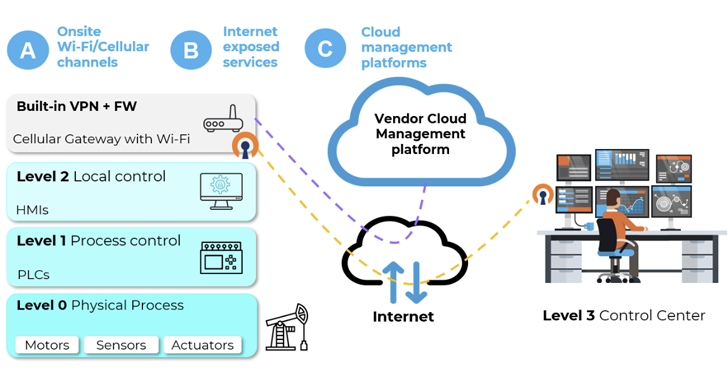
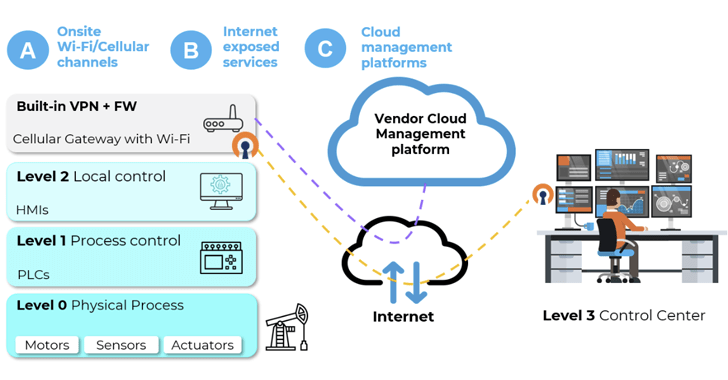
Single sign-on (SSO) is a widely-used authentication method that allows users to access multiple applications using just one set of credentials. It is considered the gold standard for security as it eliminates the need for users to remember multiple passwords and can be further secured with multi-factor authentication (MFA). In fact, an estimated 61% of attacks stem from stolen credentials, and SSO reduces the attack surface...
Read More
Risk Tag
Moyne Shire Council Detects and Halts Unauthorized Access Incident at Kindergarten. Officials at Moyne Shire Council, located in Victoria, have reported that they have identified and terminated an unauthorised access incident on a device at a council-run kindergarten. The council disclosed that the incident occurred on March 3 and targeted an "electronic device...
Read MoreNSW Health Data Breach: Payroll Information of Over 1,600 Staff Affected! NSW Health has recently confirmed that it has become the latest organisation to suffer a data breach in the Frontier Software cyber-attack at the end of 2021. According to an FAQ posted on its website, the breach has impacted staff or former staff who were employed by the Ministry of Health, as a senior executive...
Read MoreSix Law Firms Targeted in GootLoader and SocGholish Malware Campaigns Mar 01, 2023 - In January and February 2023, six different law firms were targeted in two separate threat campaigns distributing GootLoader and FakeUpdates (aka SocGholish) malware strains. GootLoader is a first-stage downloader that is capable of delivering a wide range of secondary payloads such as Cobalt Strike and ransomware. It employs search engine optimization (SEO)...
Read MoreVictoria’s auditor-general has expressed concern over the increasing number of weaknesses in IT controls in the state's local government sector. According to a new audit, the office found more IT control weaknesses due to increased scrutiny. These weaknesses included access management, policies and procedures, logging and monitoring, backup and recovery, and change management. The auditor-general noted that poor IT controls increase the risk of unauthorised access, cyber-attacks,...
Read More