Half of Orgs Use Web Application Firewalls to Paper Over Flaws
The ongoing struggle to update vulnerable software by finding and applying the right patches in a timely manner has led half of enterprise IT departments to use Web application firewalls (WAFs) either in lieu of patching or to offer some protection before patching can be achieved.
This comes from a new Dark Reading report, “How Enterprises Are Securing the Application Environment.” The survey asked 136 IT, cybersecurity, and application development professionals from organizations across more than 20 industry verticals about their application development practices.
The difficulty of finding and applying security patches is well known. In a recent series of ransomware reports, cyber-risk management company Black Kite noted that patch management was a continuing weakness across industries as varied as pharmaceuticals and auto manufacturing. While safe and reliable automation is in development, IT departments often have to make do with risk-based management and harm-reducing workarounds.
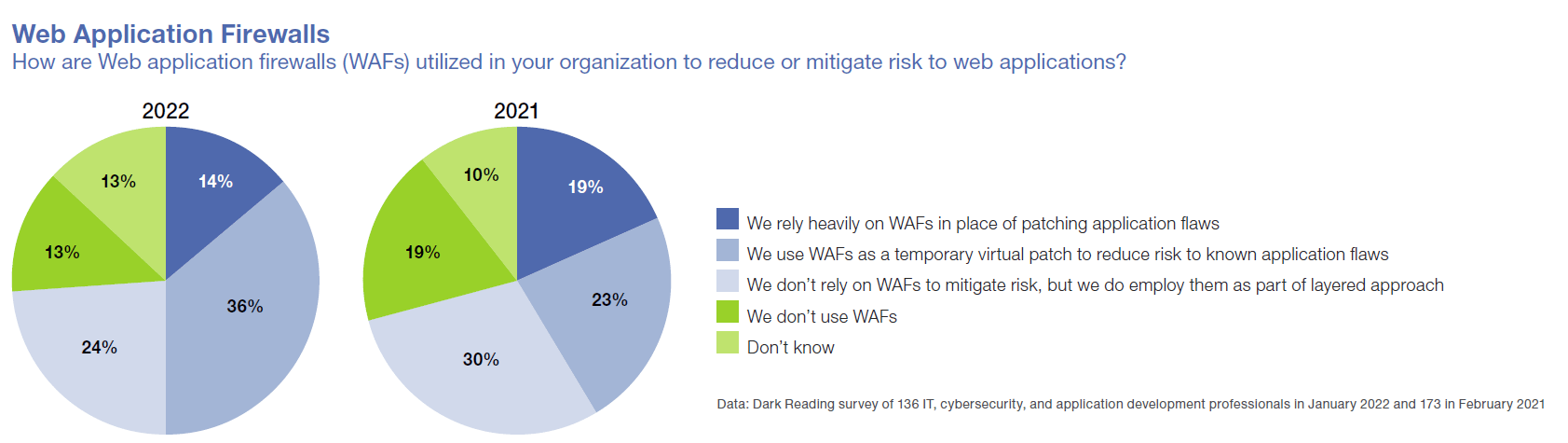
When the Dark Reading survey asked respondents in 2022 how they use WAFs to reduce risk to their Web applications, 14% admit to using WAFs instead of patching flaws, and 36% say they use WAFs as a temporary safeguard before getting around to patching. Still, that’s an improvement over 2021, when the numbers were 19% and 23%.
How enterprises employ WAFs shifted more than the number of companies that use the tool. The percentage of respondents who say they use WAFs as a part of layered defenses rather than as a kind of temporary patch dropped from 30% in 2021 to 24% in 2022. However, the total percent of those who use WAFs stayed nearly the same — 74% in 2022 versus 72% in 2021. It seems that despite the technology’s shortcomings, WAFs continue to be useful ingredients in the cybersecurity pantry.
Full article attribution is made to its original source and author.

