The Australian Government is taking steps to become the most cyber secure country in the world by 2030, with the announcement of a new national office for cyber security and the launch of a consultation on a seven-year cyber security strategy. Home Affairs Minister Clare O’Neil said the office would be led by a new senior official with the title of coordinator for cyber security, with...
Read More
Security Tag
Victoria’s auditor-general has expressed concern over the increasing number of weaknesses in IT controls in the state's local government sector. According to a new audit, the office found more IT control weaknesses due to increased scrutiny. These weaknesses included access management, policies and procedures, logging and monitoring, backup and recovery, and change management. The auditor-general noted that poor IT controls increase the risk of unauthorised access, cyber-attacks,...
Read MoreToday, Google announced that it is working with ecosystem partners to strengthen the security of firmware that interacts with Android. This is part of the company's defense-in-depth strategy, which seeks to protect the platform from malicious attacks. The Android operating system runs on what is known as the application processor (AP), but it is only one of many processors on a system-on-chip (SoC). These processors are...
Read MoreThe security of Fortinet FortiNAC appliances is under attack, with proof-of-concept exploit code now available and active exploitation attempts in the wild. FortiNAC is a zero-trust network access solution that can be deployed both as a hardware device or as a virtual machine appliance, and is used for network segmentation, visibility, and control of devices and users connected to the network. With more than 700,000 Fortinet...
Read MoreMedibank has suffered a financial blow of up to $45 million as a result of a security breach in October. The attack saw an intruder gain access to the insurer's systems using a misconfigured firewall, bypassing the need for a digital security certificate. In response, Medibank has implemented additional security measures, including increased internal and third-party monitoring, and re-examining data management in light of potential changes...
Read MoreOn February 23, 2023, multiple threat actors have been observed exploiting a critical security vulnerability impacting several Zoho ManageEngine products since January 20, 2023. Tracked as CVE-2022-47966 (CVSS score: 9.8), the remote code execution flaw allows a complete takeover of the susceptible systems by unauthenticated attackers. Martin Zugec of Bitdefender's cybersecurity firm revealed in a technical advisory that the vulnerability "allows unauthenticated remote code execution due...
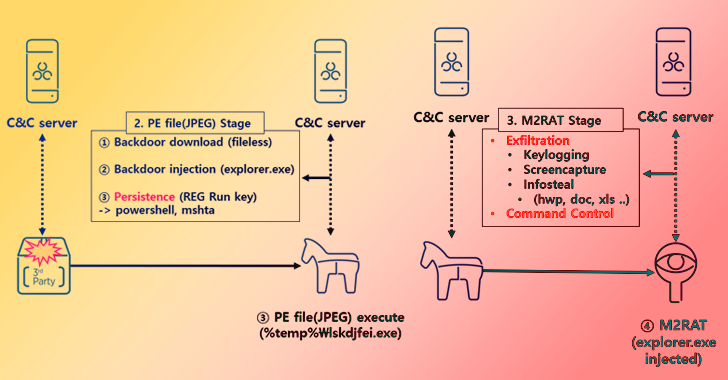
Read MoreChina-based cyberespionage actor DEV-0147 has been observed compromising diplomatic targets in South America, according to Microsoft’s Security Intelligence team. The initiative is “a notable expansion of the group’s data exfiltration operations that traditionally targeted gov’t agencies and think tanks in Asia and Europe,” the team tweeted on Monday. DEV-0147’s attacks in South America included post-exploitation activity involving the abuse of on-premises identity infrastructure for reconnaissance...