




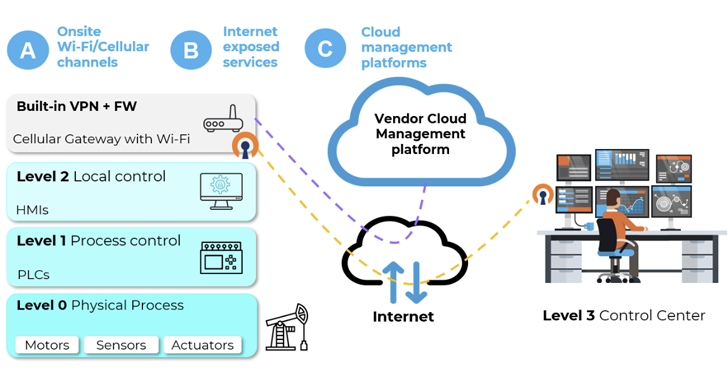
A report released this week by OpinionMatters and commissioned by Noname Security found that more than three out of four senior cybersecurity professionals in the US and UK said that their organization had experienced at least one API-related security incident within the last 12 months. A similar number, 74%, said that they had not completed a full inventory of all APIs in their systems, or have...
Read MoreThe cost of a data breach is not easy to define, but as more organizations fall victim to attacks and exposures, the potential financial repercussions are becoming clearer. For modern businesses of all shapes and sizes, the monetary impact of suffering a data breach is substantial. IBM’s latest Cost of a Data Breach report discovered that, in 2022, the average cost of a data breach...
Read MoreWhat is SSO? Single sign-on (SSO) is a centralized session and user authentication service in which one set of login credentials can be used to access multiple applications. Its beauty is in its simplicity; the service authenticates you on one designated platform, enabling you to then use a variety of services without having to log in and out each time. In the most common arrangement, the identity...
Read MoreSourcing and keeping appropriate staff may be critical to improving cybersecurity capabilities, but as economic uncertainty and difficult labour markets buffet businesses this year experts warn that businesses must make “systemic changes” to meet their staffing requirements. The economic uncertainty was highlighted by a recent Australian Information Industry Association (AIIA) member survey that found 47% of businesses expressed confidence in the economy this year, compared with...
Read MoreDespite a recent decline in attacks, ransomware still poses significant threats to enterprises, as the attacks against healthcare organizations demonstrated this month. It is also becoming more capable. In particular, ransomware writers are aware that backups are an effective defense and are modifying their malware to track down and eliminate the backups. Ransomware targeting backups Ransomware will now delete any backups it happens to come across along...
Read MoreOne of the smartest moves you can make to protect employees, especially those working from home, is to encourage them to use a password manager. It’s one of the easiest, too. Keyword best practices pertain to complexity, change frequency and uniqueness. Each best practice is intended to mitigate known attack methods and harden your online identities to both prevent compromise and limit the damage if account...
Read More