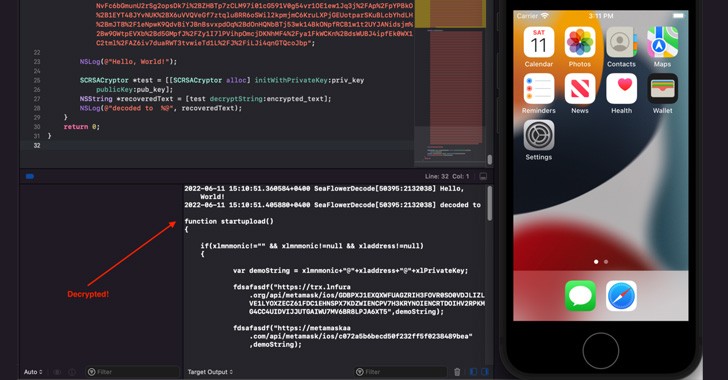
A technically sophisticated threat actor known as SeaFlower has been targeting Android and iOS users as part of an extensive campaign that mimics official cryptocurrency wallet websites intending to distribute backdoored apps that drain victims' funds. Said to be first discovered in March 2022, the cluster of activity "hint[s] to a strong relationship with a Chinese-speaking entity yet to be uncovered," based on the macOS usernames,...
Read More
Cybersecurity
Intel has introduced a reference design it says can enable accelerator cards for security workloads including secure access service edge (SASE), IPsec, and SSL/TLS. The upside of the server cards would be offloading some application processing from CPUs, effectively increasing server performance without requiring additional server rack space, according to Intel. The announcement was made at RSA Conference 2022, and details were published in a blog post...
Read MoreThe notorious Emotet malware has turned to deploy a new module designed to siphon credit card information stored in the Chrome web browser. The credit card stealer, which exclusively singles out Chrome, has the ability to exfiltrate the collected information to different remote command-and-control (C2) servers, according to enterprise security company Proofpoint, which observed the component on June 6. The development comes amid a spike in Emotet...
Read MoreWhat is SSO? Single sign-on (SSO) is a centralized session and user authentication service in which one set of login credentials can be used to access multiple applications. Its beauty is in its simplicity; the service authenticates you on one designated platform, enabling you to then use a variety of services without having to log in and out each time. In the most common arrangement, the identity...
Read MoreSourcing and keeping appropriate staff may be critical to improving cybersecurity capabilities, but as economic uncertainty and difficult labour markets buffet businesses this year experts warn that businesses must make “systemic changes” to meet their staffing requirements. The economic uncertainty was highlighted by a recent Australian Information Industry Association (AIIA) member survey that found 47% of businesses expressed confidence in the economy this year, compared with...
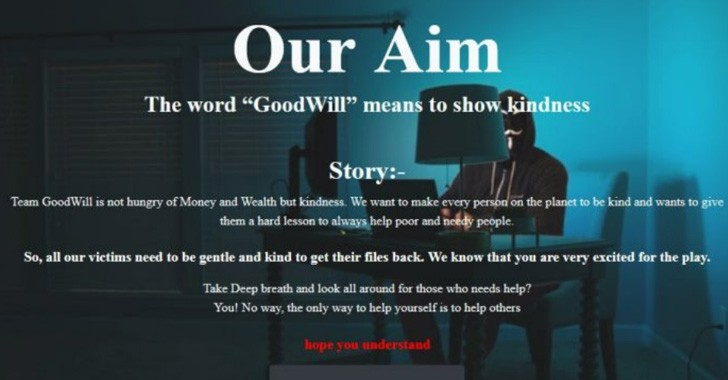
Read MoreCybersecurity researchers have disclosed a new ransomware strain called GoodWill that compels victims into donating for social causes and provide financial assistance to people in need. "The ransomware group propagates very unusual demands in exchange for the decryption key," researchers from CloudSEK said in a report published last week. "The Robin Hood-like group claims to be interested in helping the less fortunate, rather than extorting victims...
Read MoreA pair of critical flaws in industrial Internet of Things data platform vendor Open Automation Software (OAS) are threatening industrial control systems (ICS), according to Cisco Talos. They're part of a group of eight vulnerabilities in OAS software that the vendor patched this week. Among the flaws is one (CVE-2022-26082) that gives attackers the ability to remotely execute malicious code on a targeted machine to disrupt or alter its...
Read MoreIntel revealed a string of security advancements at its inaugural Intel Vision event this week, including Project Amber — a security as a service initiative for confidential computing — as well as increased collaboration for secure and responsible developments in AI, and a phased approach to quantum-safe cryptography. Project Amber is aimed at providing organizations with remote verification of security in cloud, edge, and on-premises environments. "As...
Read MoreBLACK HAT ASIA — A soda can, a smartphone stand, or any shiny, lightweight desk decoration could pose a threat of eavesdropping, even in a soundproof room, if an attacker can see the object, according to a team of researchers from Ben-Gurion University of the Negev. At the Black Hat Asia security conference on Thursday, and aiming to expand on previous research into optical speech eavesdropping, the...
Read MoreThe maintainers of the RubyGems package manager have addressed a critical security flaw that could have been abused to remove gems and replace them with rogue versions under specific circumstances. "Due to a bug in the yank action, it was possible for any RubyGems.org user to remove and replace certain gems even if that user was not authorized to do so," RubyGems said in a security...
Read More