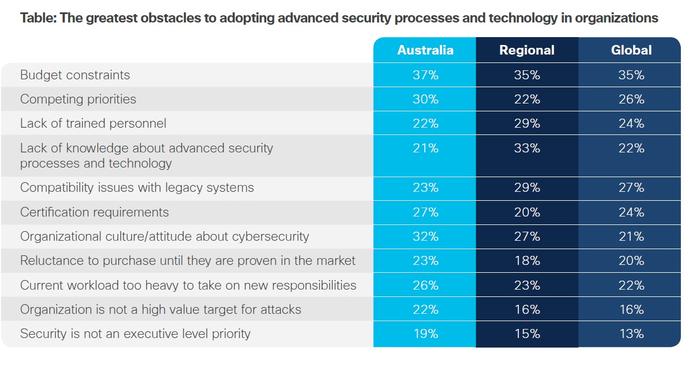
Australian organisations are struggling to defend against cyber threats according to a recent study. A total of 209 Australian CISOs responded to the annual Cisco Asia Pacific CISO Benchmark Study on the cyber security landscape with 65 per cent saying they are suffering from cyber security fatigue or are receiving so many daily threats they have given up proactively defending against them. Australian organisations are receiving a...
Read More
Cybersecurity
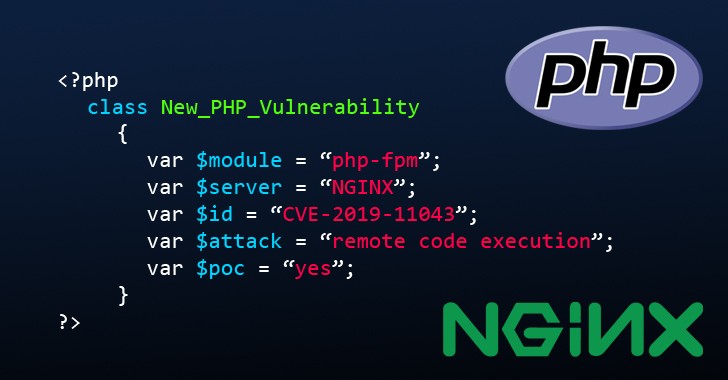
If you're running any PHP based website on NGINX server and have PHP-FPM feature enabled for better performance, then beware of a newly disclosed vulnerability that could allow unauthorised attackers to hack your website server remotely. The vulnerability, tracked as CVE-2019-11043, affects websites with certain configurations of PHP-FPM that is reportedly not uncommon in the wild and could be exploited easily as a proof-of-concept (PoC) exploit...
Read MoreCVE-2017-11882 has been attackers' favorite malware delivery mechanism throughout the second and third quarters of 2019. The third quarter of 2019 brought the rise of keylogger Agent Tesla, the decline of phishing-delivered ransomware-as-a-service (RaaS), and attackers' continued preference for exploiting the CVE-2017-11882 Microsoft Office vulnerability to deliver phishing campaigns. Emotet began to surge toward the end of last quarter, according to Cofense's Q3 2019 Malware Trends Report,...
Read MoreThe Australian Signals Directorate’s Australian Cyber Security Centre (ACSC) is investigating a widespread malware campaign known as Emotet.Emotet is a Trojan virus delivered via emails sent with malicious attachments.Cyber criminals use malware for different reasons, most commonly to steal personal or valuable information from which they can profit, hold recipients to ransom or install damaging programs onto devices without your knowledge.Email users should always exercise...
Read MoreThe recent controversies surrounding the WhatsApp hacking haven't yet settled, and the world's most popular messaging platform could be in the choppy waters once again. The Hacker News has learned that last month WhatsApp quietly patched yet another critical vulnerability in its app that could have allowed attackers to remotely compromise targeted devices and potentially steal secured chat messages and files stored on them. The vulnerability — tracked...
Read MoreThe security landscape is never static. Smarter cybercriminals, evolving malware, more regulations and higher financial and national security stakes force organizations and their security teams to constantly adjust priorities. The IDG 2019 Security Priorities Study, released at the end of July 2019, helps to define how those priorities are changing for the next 12 months. The study is based on a survey of 528 security professionals...
Read MoreA team of German cybersecurity researchers has discovered a new cache poisoning attack against web caching systems that could be used by an attacker to force a targeted website into delivering error pages to most of its visitors instead of legitimate content or resources. The issue affects reverse proxy cache systems like Varnish and some widely-used Content Distribution Networks (CDNs) services, including Amazon CloudFront, Cloudflare, Fastly,...
Read MoreIn rush to fix newly discovered security issues, developers are neglecting to address older ones, Veracode study finds. The latest edition of Veracode's annual "State of Software Security" study released this week shows that many enterprise organizations are at increased breach risk because of aging, unaddressed application security flaws. Veracode recently analyzed data from application security tests on more than 85,000 applications and found that, on average,...
Read MoreCisco this week said it issued a software update to address a vulnerability in its Cisco REST API virtual service container for Cisco IOS XE software that scored a critical 10 out of 10 on the Common Vulnerability Scoring System (CVSS) system. With the vulnerability an attacker could submit malicious HTTP requests to the targeted device and if successful, obtain the token-id of an authenticated user....
Read MoreThe Australian Signals Directorate (ASD)’s Australian Cyber Security Centre (ACSC) has released updates to the Australian Government Information Security Manual (ISM) to help organisations set the strategic framework for protecting their systems and information from cyber threats.Updated monthly, the ISM is created primarily for Chief Information Security Officers and cyber security professionals to keep up-to-date with current cyber security risks and appropriate mitigation strategies.The ISM...
Read More